Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
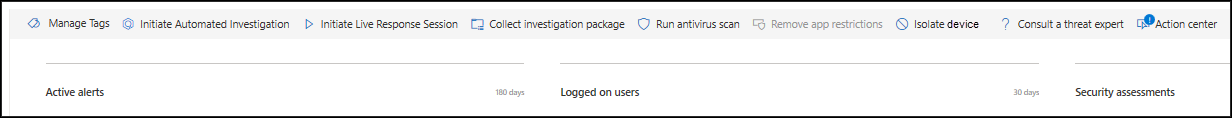
Quickly respond to detected attacks by isolating devices or collecting an investigation package. After taking action on devices, you can check activity details on the Action center.
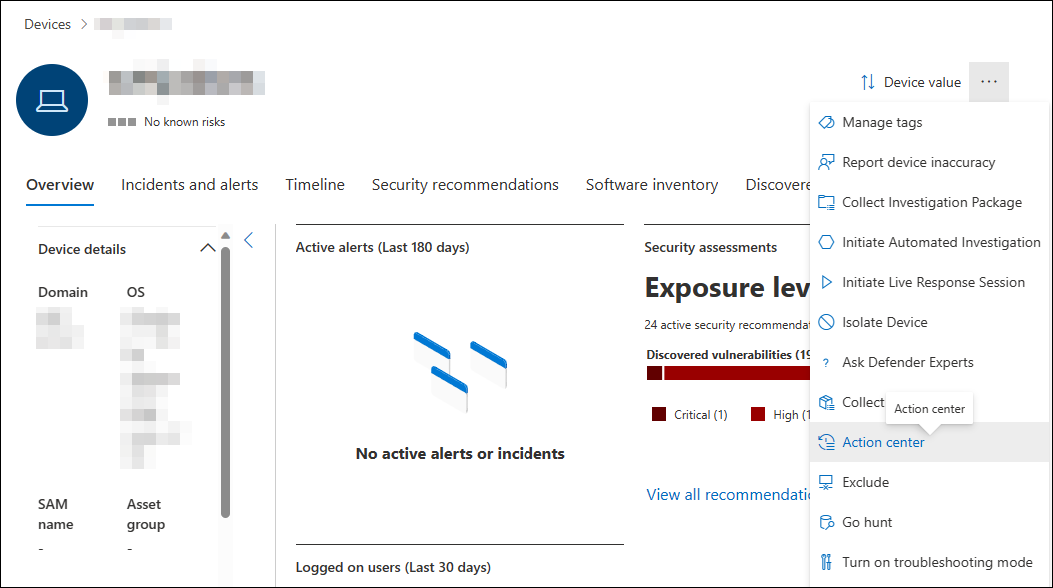
Response actions run along the top of a specific device page and include:

Defender for Endpoint Plan 1 includes only the following manual response actions:
Microsoft Defender for Business does not include the "Stop and quarantine a file" action at this time.
Your subscription must include Defender for Endpoint Plan 2 to have all of the response actions described in this article.
You can find device pages from any of the following views:
For information on availability and support for each response action, please refer to the supported/minimum operating system requirements found under each feature.
Add or manage tags to create a logical group affiliation. Device tags support proper mapping of the network, enabling you to attach different tags to capture context and to enable dynamic list creation as part of an incident.
For more information on device tagging, see Create and manage device tags.
You can start a new general purpose automated investigation on the device if needed. While an investigation is running, any other alert generated from the device will be added to an ongoing Automated investigation until that investigation is completed. In addition, if the same threat is seen on other devices, those devices are added to the investigation.
For more information on automated investigations, see Overview of Automated investigations.
Live response is a capability that gives you instantaneous access to a device by using a remote shell connection. This gives you the power to do in-depth investigative work and take immediate response actions to promptly contain identified threats in real time.
Live response is designed to enhance investigations by enabling you to collect forensic data, run scripts, send suspicious entities for analysis, remediate threats, and proactively hunt for emerging threats.
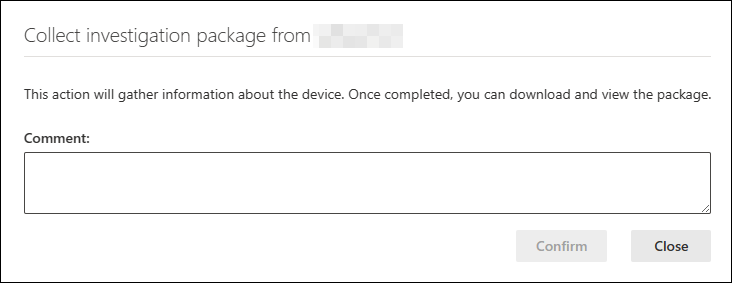
As part of the investigation or response process, you can collect an investigation package from a device. By collecting the investigation package, you can identify the current state of the device and further understand the tools and techniques used by the attacker.
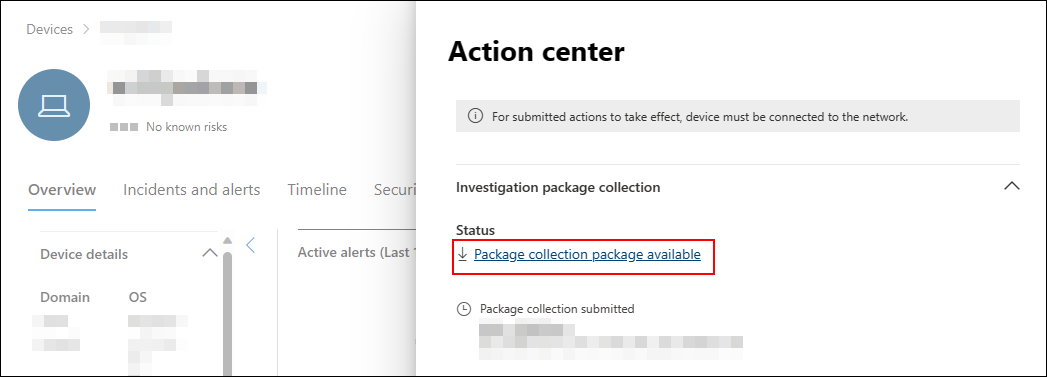
To download the package (Zip file) and investigate the events that occurred on a device:

 For Windows devices, the package contains the following folders:
For Windows devices, the package contains the following folders:| Folder | Description |
|---|---|
| Autoruns | Contains a set of files that each represent the content of the registry of a known auto start entry point (ASEP) to help identify attacker's persistency on the device. |
NOTE: If the registry key is not found, the file will contain the following message: "ERROR: The system was unable to find the specified registry key or value."
NOTE: The pfirewall.log file must exist in %windir%\system32\logfiles\firewall\pfirewall.log, so it will be included in the investigation package. For more information on creating the firewall log file, see Configure the Windows Defender Firewall with Advanced Security Log
Contains files for SMBInboundSessions and SMBOutboundSession.
NOTE: If there are no sessions (inbound or outbound), you'll get a text file that tells you that there are no SMB sessions found.
This can help to track suspicious files that an attacker may have dropped on the system.
NOTE: If the file contains the following message: "The system cannot find the path specified", it means that there is no temp directory for this user, and might be because the user didn't log in to the system.
The collection packages for macOS and Linux devices contain the following:
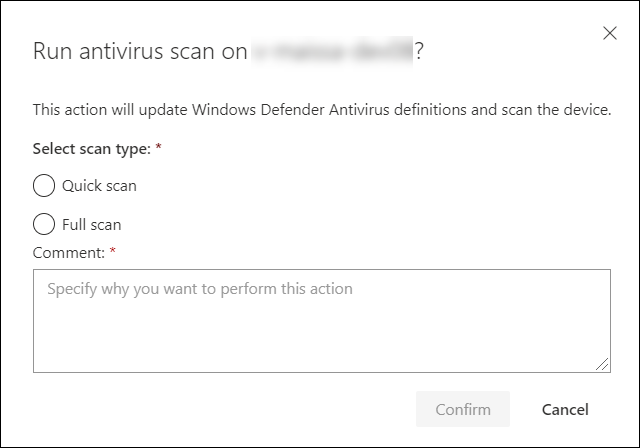
As part of the investigation or response process, you can remotely initiate an antivirus scan to help identify and remediate malware that might be present on a compromised device.
One you have selected Run antivirus scan, select the scan type that you'd like to run (quick or full) and add a comment before confirming the scan.
The Action center will show the scan information and the device timeline will include a new event, reflecting that a scan action was submitted on the device. Microsoft Defender Antivirus alerts will reflect any detections that surfaced during the scan.
When triggering a scan using Defender for Endpoint response action, Microsoft Defender antivirus 'ScanAvgCPULoadFactor' value still applies and limits the CPU impact of the scan. If ScanAvgCPULoadFactor is not configured, the default value is a limit of 50% maximum CPU load during a scan. For more information, see configure-advanced-scan-types-microsoft-defender-antivirus.
In addition to containing an attack by stopping malicious processes, you can also lock down a device and prevent subsequent attempts of potentially malicious programs from running.
To restrict an application from running, a code integrity policy is applied that only allows files to run if they are signed by a Microsoft issued certificate. This method of restriction can help prevent an attacker from controlling compromised devices and performing further malicious activities.
You'll be able to reverse the restriction of applications from running at any time. The button on the device page will change to say Remove app restrictions, and then you take the same steps as restricting app execution.
Once you have selected Restrict app execution on the device page, type a comment and select Confirm. The Action center will show the scan information and the device timeline will include a new event.
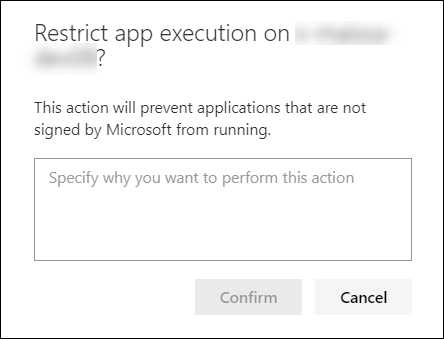
When an app is restricted, the following notification is displayed to inform the user that an app is being restricted from running:
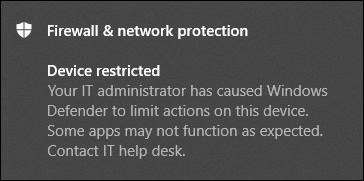
The notification is not available on Windows Server 2016 and Windows Server 2012 R2.
Depending on the severity of the attack and the sensitivity of the device, you might want to isolate the device from the network. This action can help prevent the attacker from controlling the compromised device and performing further activities such as data exfiltration and lateral movement.
This device isolation feature disconnects the compromised device from the network while retaining connectivity to the Defender for Endpoint service, which continues to monitor the device.
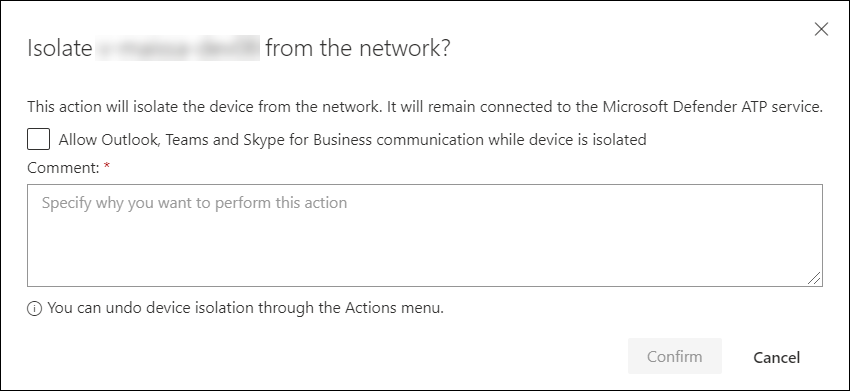
On Windows 10, version 1709 or later, you'll have more control over the network isolation level. You can also choose to enable Outlook, Microsoft Teams, and Skype for Business connectivity (a.k.a 'Selective Isolation').
You'll be able to reconnect the device back to the network at any time. The button on the device page will change to say Release from isolation, and then you take the same steps as isolating the device.
Once you have selected Isolate device on the device page, type a comment and select Confirm. The Action center will show the scan information and the device timeline will include a new event.
The device will remain connected to the Defender for Endpoint service even if it is isolated from the network. If you've chosen to enable Outlook and Skype for Business communication, then you'll be able to communicate to the user while the device is isolated. Selective isolation only works on the classic versions of Outlook and Microsoft Teams.
The device isolation feature is an invaluable tool for safeguarding devices against external threats. However, there are instances when isolated devices become unresponsive.
There's a downloadable script for these instances that you can run to forcibly release devices from isolation. The script is available through a link in the UI.
To forcibly release device from isolation:
The minimum requirements for 'forcibly release device from isolation' feature are:
When a device is being isolated, the following notification is displayed to inform the user that the device is being isolated from the network:
The notification is not available on non-Windows platforms.
When you have identified an unmanaged device that is compromised or potentially compromised, you might want to contain that device from the network. When you contain a device any Microsoft Defender for Endpoint onboarded device will block incoming and outgoing communication with that device. This action can help prevent neighboring devices from becoming compromised while the security operations analyst locates, identifies, and remediates the threat on the compromised device.
Blocking incoming and outgoing communication with a 'contained' device is supported on onboarded Microsoft Defender for Endpoint Windows 10 and Windows Server 2019+ devices.
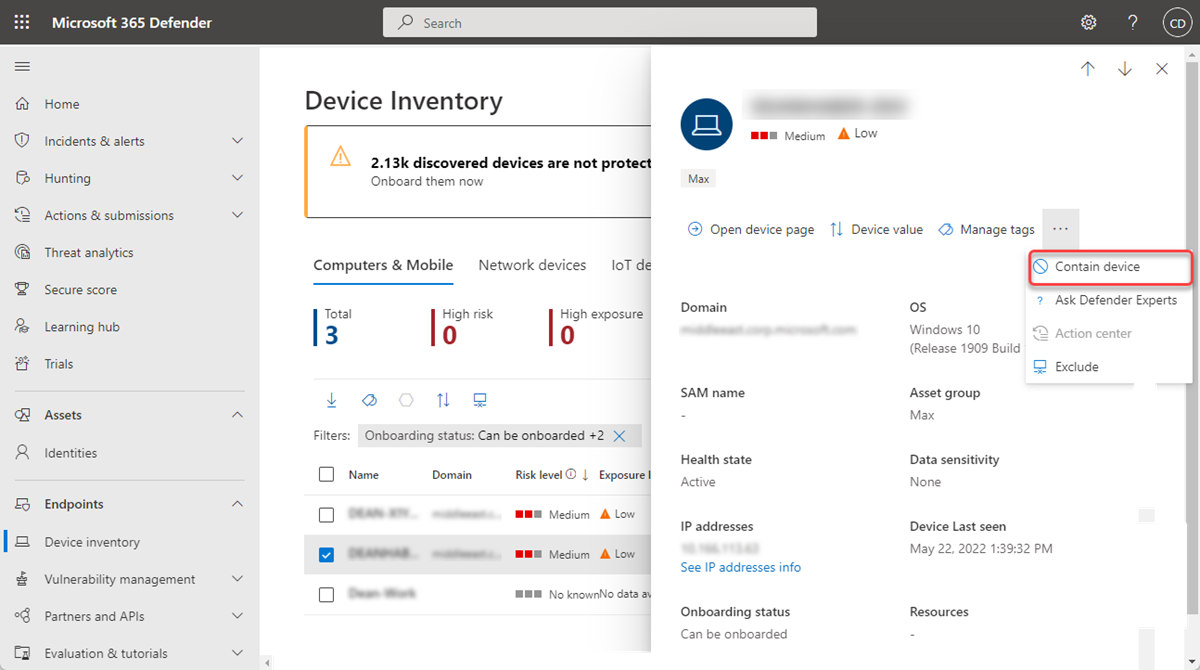
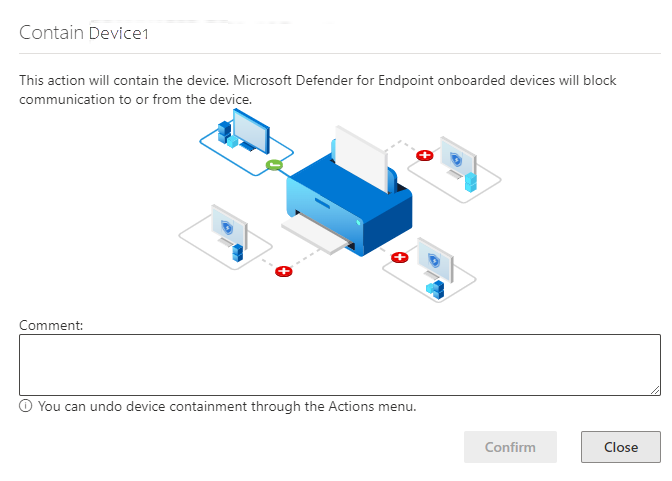
A device can also be contained from the device page by selecting Contain device from the action bar:
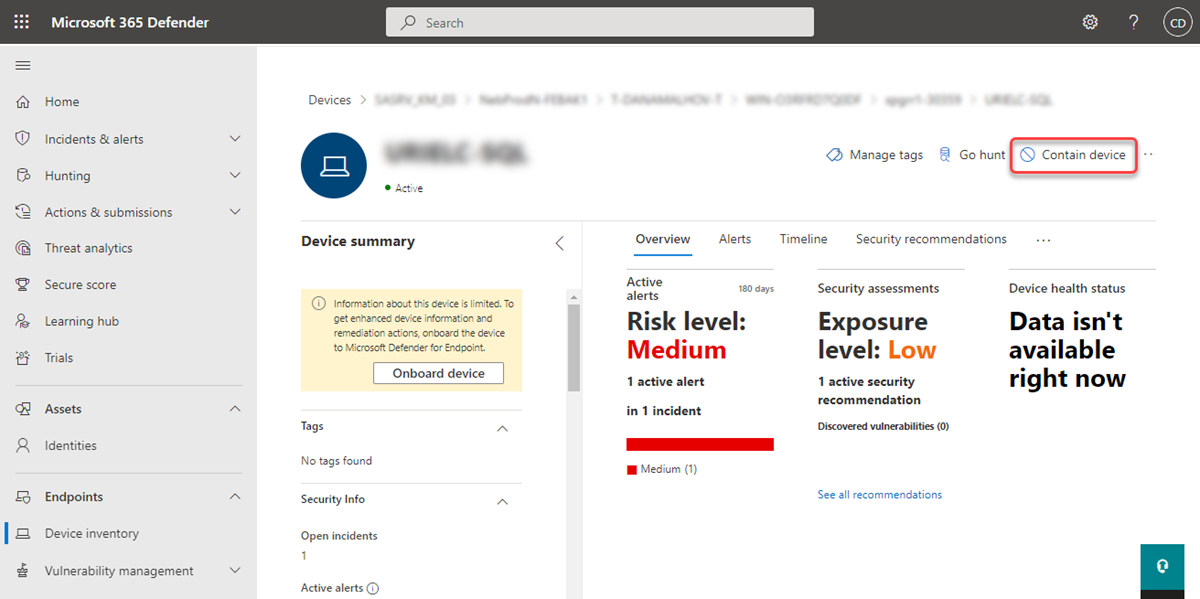
It can take up to 5 minutes for the details about a newly contained device to reach Microsoft Defender for Endpoint onboarded devices.
After you contain a device, if the behavior isn't as expected, verify the Base Filtering Engine (BFE) service is enabled on the Defender for Endpoint onboarded devices.
You'll be able to stop containing a device at any time.
When an identity in your network might be compromised, you must prevent that identity from accessing the network and different endpoints. Defender for Endpoint can "contain" an identity, blocking it from access, and helping prevent attacks-- specifically, ransomware. When an identity is contained, any supported Microsoft Defender for Endpoint onboarded device will block incoming traffic in specific protocols related to attacks (network logons, RPC, SMB, RDP), terminate ongoing remote sessions and logoff existing RDP connections (termination the session itself including all its related processes), while enabling legitimate traffic. This action can significantly help to reduce the impact of an attack. When an identity is contained, security operations analysts have extra time to locate, identify and remediate the threat to the compromised identity.
Blocking incoming communication with a "contained" user is supported on onboarded Microsoft Defender for Endpoint Windows 10 and 11 devices (Sense version 8740 and higher), Windows Server 2019+ devices, and Windows Servers 2012R2 and 2016 with the modern agent.
Once a Contain user action is enforced on a domain controller, it starts a GPO update on the Default Domain Controller policy. A change of a GPO starts a sync across the domain controllers in your environment. This is expected behavior, and if you monitor your environment for AD GPO changes, you may be notified of such changes. Undoing the Contain user action reverts the GPO changes to their previous state, which will then start another AD GPO synchronization in your environment. Learn more about merging of security policies on domain controllers.
Currently, containing users is only available automatically by using automatic attack disruption. When Microsoft detects a user as being compromised a "Contain User" policy is automatically set.
After a user is contained, you can view the action in this History view of the Action Center. Here, you can see when the action occurred, and which users in your organization were contained:
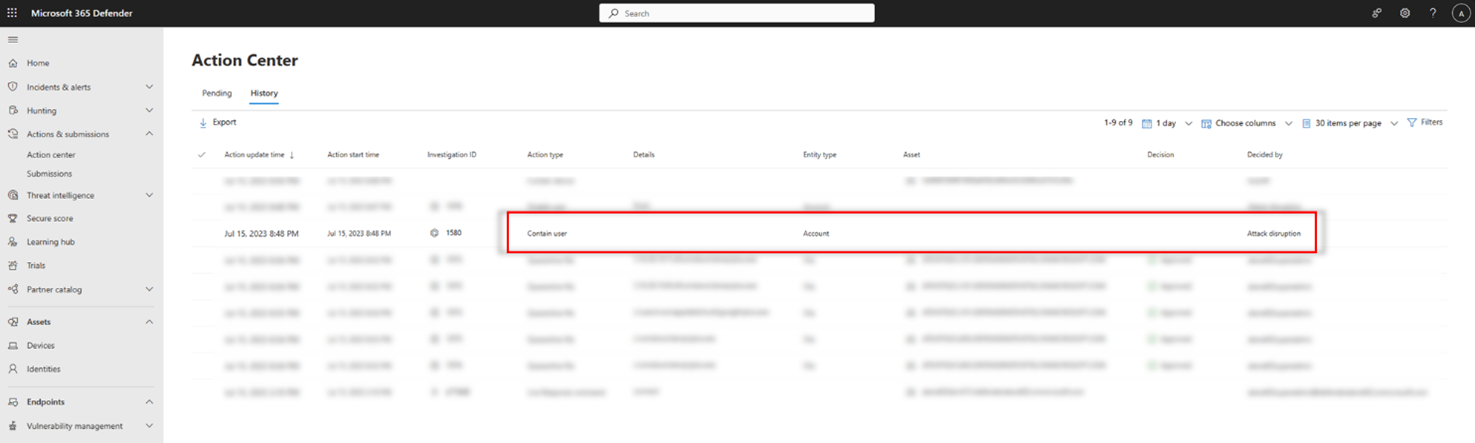
Furthermore, after an identity is considered "contained", that user will be blocked by Defender for Endpoint and cannot perform any malicious lateral movement or remote encryption on or to any supported Defender for Endpoint onboarded device. These blocks will show up as alerts to help you quickly see the devices the compromised user attempted access and potential attack techniques:
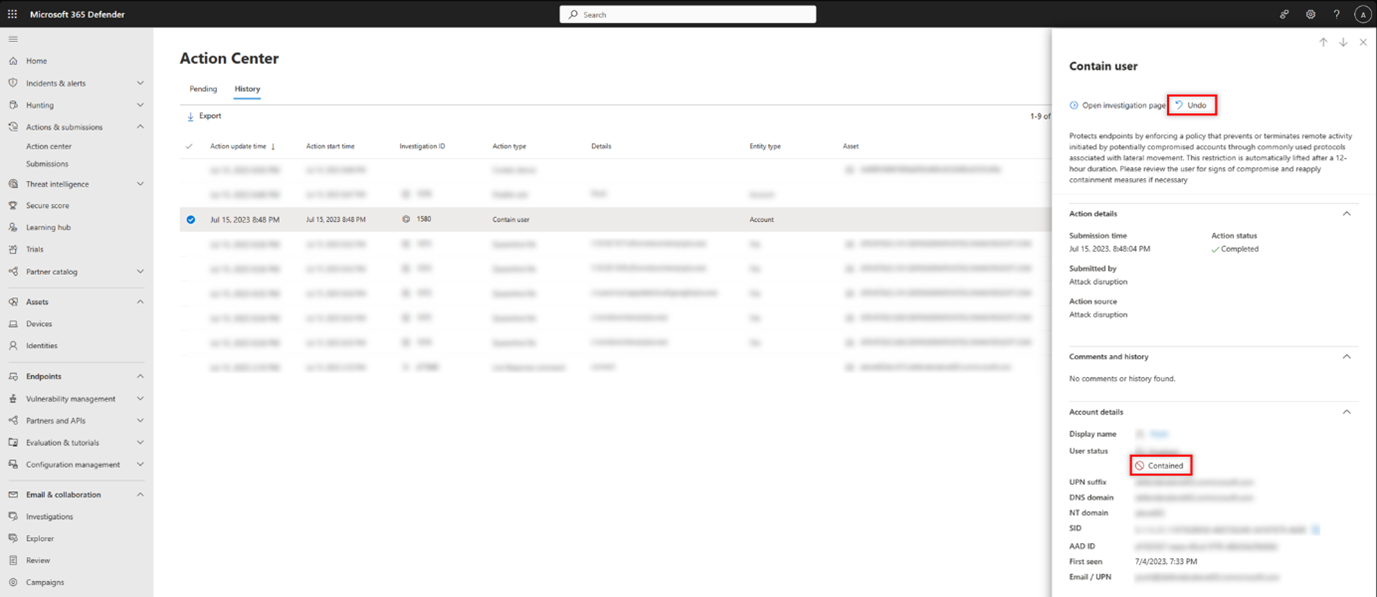
You can release the blocks and containment on a user at any time:
This action will restore this user's connection to the network.
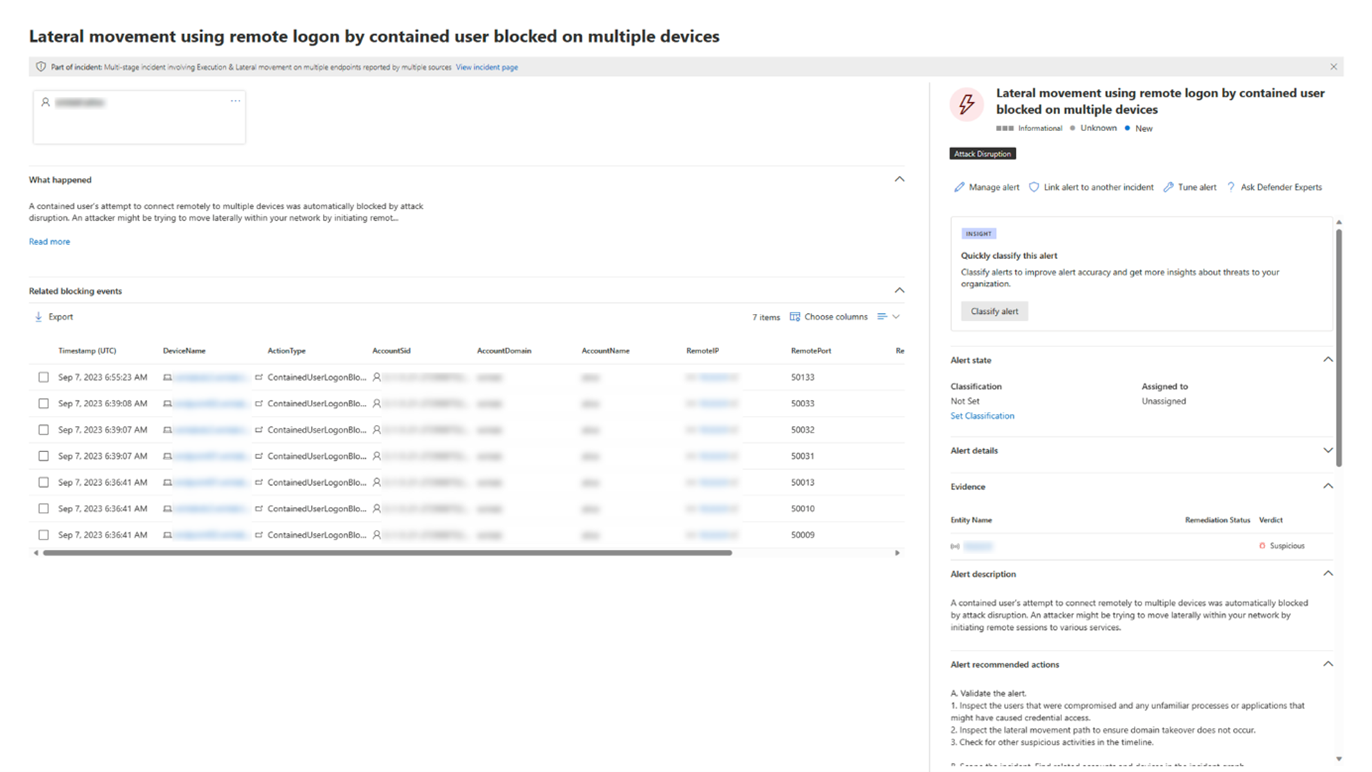
After a user is contained, you can investigate the potential threat by viewing the blocked actions by the compromised user. In the Device timeline view, you can see information about specific events, including protocol and interface granularity, and the relevant MITRE Technique associated it.
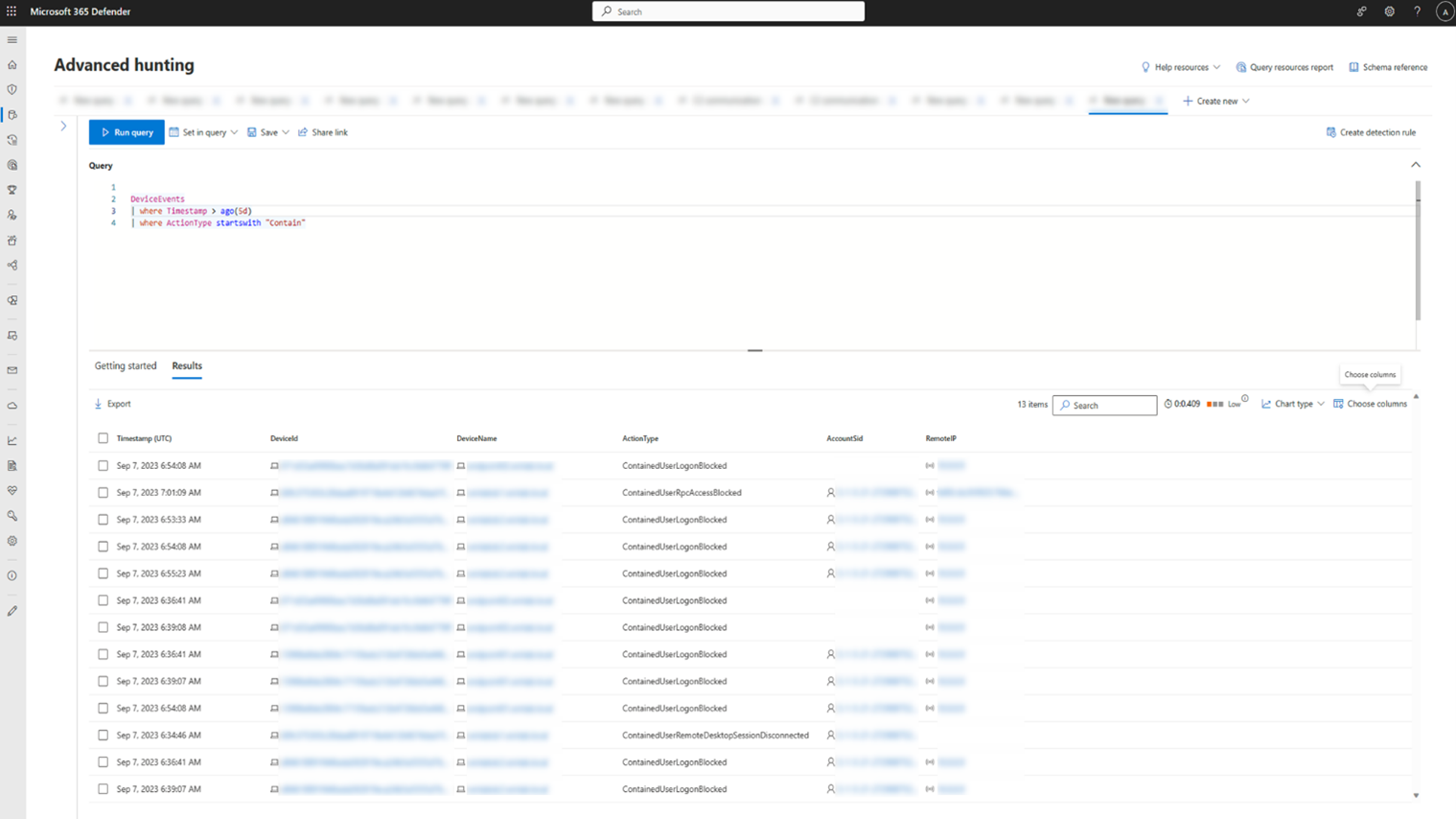
In addition, you can expand the investigation by using Advanced Hunting. Look for any "Action Type" starting with "Contain" in the "DeviceEvents" table. Then, you can view all the different singular blocking events in relation to Contain User in your tenant, dive deeper into the context of each block, and extract the different entities and techniques associated with those events.
You can consult a Microsoft threat expert for more insights regarding a potentially compromised device or already compromised ones. Microsoft Threat Experts can be engaged directly from within the Microsoft Defender XDR for timely and accurate response. Experts provide insights not just regarding a potentially compromised device, but also to better understand complex threats, targeted attack notifications that you get, or if you need more information about the alerts, or a threat intelligence context that you see on your portal dashboard.
The Action center provides information on actions that were taken on a device or file. You'll be able to view the following details:
All other related details are also shown, for example, submission date/time, submitting user, and if the action succeeded or failed.
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.